MANAGED SERVICES
Information Technology Services for Small to Medium Business
SECURITY
To be competitive in today's dynamic Internet economy, companies must balance the need of securing their internal data, as well as that of their customers. In the past, having an adequate firewall, a reliable Anti-Virus/Malware product and corporate security policies were deemed sufficient to protect valuable data assets. Today’s security solutions require a much broader scope, especially given a significant increase in malware attacks via multiple methods. Additionally, small to medium businesses are increasingly becoming the focus of attacks by hackers, requiring additional security measures. CPS’ extensive security experience can assist you in designing and implementing cost efficient security measures appropriate for your company.
Since CPS’ inception in 1999, Security has been a cornerstone of our professional services. During this period we have advised client’s, both large and small, that security measures put into place need to be periodically reviewed and implement newer security measures to counter current and future threats. In particular, smaller firms have eschewed this as being too costly, or unwarranted. Several recent articles in prominent periodicals have highlighted this greater threat to smaller businesses.
With newer and more affordable technologies available, CPS’ expertise can assist your business in mitigating risk. In particular, CPS offers solutions that increasingly work together to prevent/mitigate
Ransomware.
Weak Solutions
Most companies have implemented some type of firewall within their environments, along with Anti-Virus/Malware solutions. Smaller businesses generally rely on firewalls that are built into the DSL or Cable modems to protect their internal data. However, these solutions only block or allow specific traffic (such as Email or Web based traffic). What these solutions lack is a means to look deeper into the data streams, where Malware is embedded. Small to medium businesses also tend to rely on a single Anti-Virus/Malware solution, typically installed on the firms workstations and servers. CPS has found over the years that no single vendor can adequately detect nor protect against every variant of threats that exist today. While some protection is better than none, today's complex attacks require a more comprehensive approach to securing your data
CPS Solution
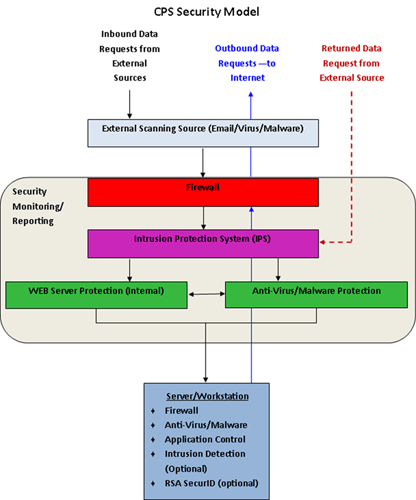
The diagram above represents a general depiction of the CPS' methodology to implementing security. Variations to this model are implemented based on a client’s security needs and budget. Our front line defense utilizes Check Point® Software Technologies. In particular, the integration of their Software Blades enables a tight, overlapping preventative security structure along with excellent monitoring and reporting features. Similar features are now available for small business through Checkpoints Small to Medium business products, at very affordable price points. As with any security solution that CPS provides, we do not solely rely on a single vendor. Surrounding the Check Point solution, CPS continually identifies and researches other vendors’ offerings that augment and enhance our recommended security model. Most of the above areas above are recommended as part of our comprehensive security strategy, while others are recommended based on regulatory compliance and/or individual client requirements. Our most common recommendations include:
- External pre-filtering services (i.e. SPAM and Anti-Virus/Malware)
- Anti-Virus/Malware
- Web Protection
- Application Protection
- Intrusion Protection
- Timely patching of systems throughout the network
- Data Encryption
- 2FA (Two-Factor Authentication)
- Disaster Recovery
While Disaster recovery has always being part of a comprehensive solution for our clients. The introduction of Ransomware threat to corporate data has resulted in our adding Disaster Recovery to CPS' Security recommendations as our recommended vendor has implemented safeguards that assist in mitigating Ransomware attacks across multiple variants.
Get in Contact with Us Today!

Mailing Address
P.O. BOX 2047
Woodstock, GA 30188
Headquarters
270 Scientific Drive
Suite 3
Norcross, GA 30092
Main Office
All Rights Reserved | Complete Protocol Solutions